Encryption
(Diagram was created by me)
Encryption is used to keep data secure when it’s being transmitted. There are a variety of different methods which can be used to scramble data before it’s transmitted and then decipher it once it arrives at its destination. We’re going to look at symmetric and asymmetric encryption.
Cryptography is everywhere
Secure Communication
web traffic: HTTPS
wireless traffic: 802.11i WPA2 (and WEP), GSM, Bluetooth
Encrypting files on disk: EFS, TrueCrypt
Content protection (e.g. DVD, Blu-ray): CSS, AACS
User authentication… and much much more
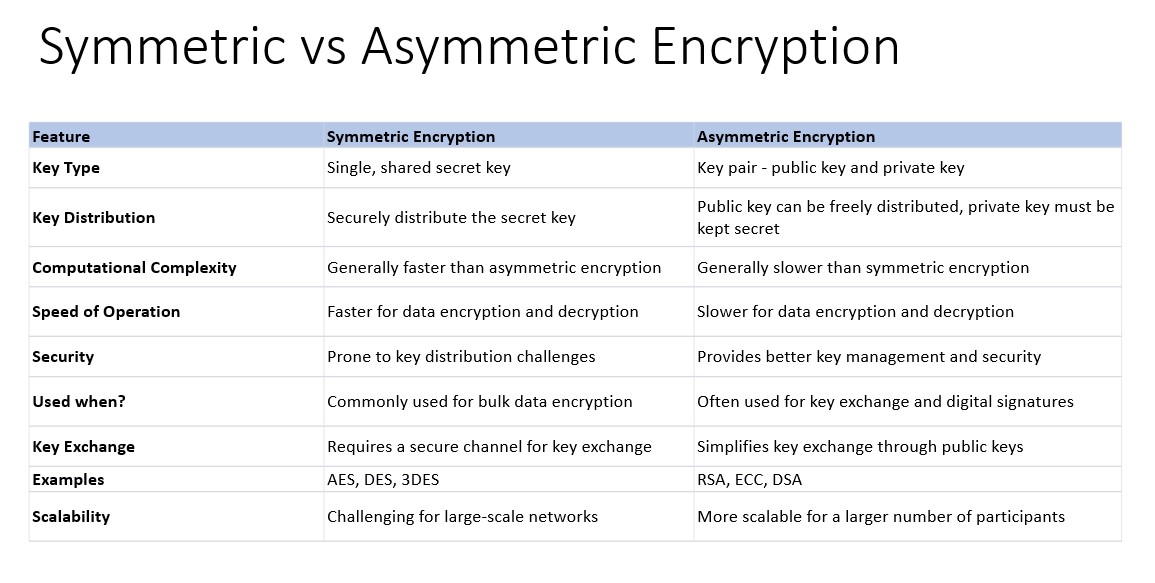
Symmetric Encryption
In symmetric encryption, both the sender and receiver share the same private key, which they distribute to each other in a process called a key exchange. This key is used for both encrypting and decrypting data. It’s important that the private key is kept secret. If the key is intercepted during the key exchange, then any communications sent can be intercepted and decrypted using the key. Asymmetric encryption gets around this issue.
Asymmetric Encryption
When sending information using asymmetric encryption, two keys are used: one public and a second, private, key. The public key can be published anywhere, free for the world to see, while the private key must be kept secret. Together, these keys are known as a key pair and are mathematically related to one another.
In contrast to symmetric encryption, a single key cannot be used to both encrypt and decrypt communication. Instead, messages encrypted with the recipient’s public key can only be decrypted with the recipient’s private key, which should only be in the possession of the recipient. If someone wants to send you a message, they must first find your public key. There are a variety of websites which can do this for you. The message is then encrypted with your public key meaning that only you can decrypt it.
If you want to prove that a message has been sent by you, you can encrypt it using your private key. This means that anyone can decrypt it (as your public key is available to anyone) and by doing so, can guarantee that you encrypted the message, as only you have access to the private key.
This forms the basis of a system called digital signatures.